Understanding Threat Intelligence in Cyber Security
What do you mean by Threat Intelligence?
Threat intelligence is a term that refers to the information collected, analyzed, and disseminated about Potential or current cyber threats that could compromise the security of an organization’s digital assets. This information can come from a variety of sources, including security vendors, government agencies, industry groups, and even the dark web.
How does Threat Intelligence work?
Threat intelligence works by gathering data on known threats, vulnerabilities, and potential risks to an organization’s systems and networks. This data is then analyzed to identify patterns and trends that could indicate a potential security threat. This information is then used to inform security measures and protocols to protect against these threats.
What is known about Threat Intelligence?
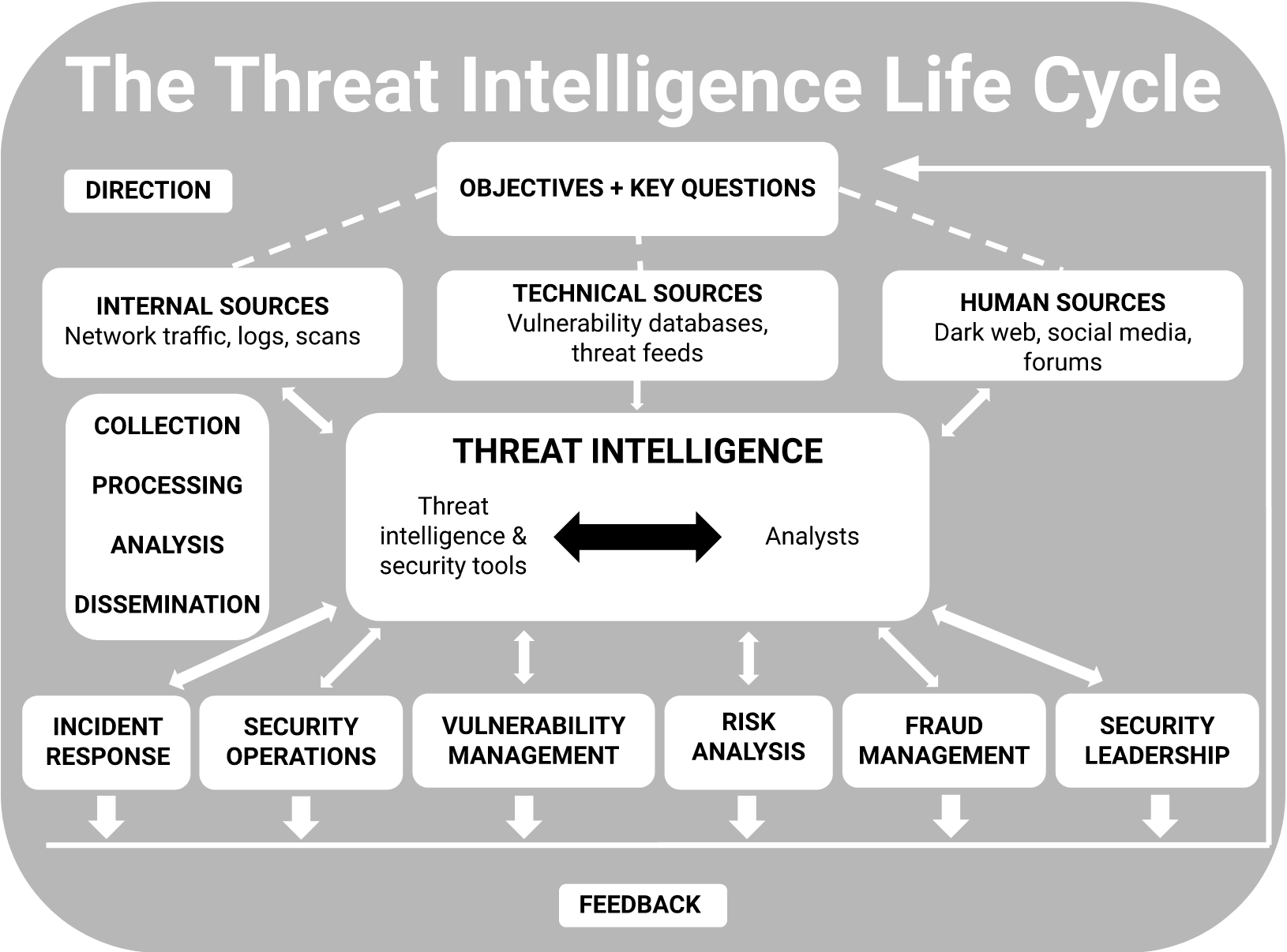
Image Source: sentinelone.com
Threat intelligence is a critical component of any organization’s cyber security strategy. By staying informed about current and emerging threats, organizations can proactively defend against cyber attacks and minimize their risk of a breach. Threat intelligence also helps organizations understand the tactics, techniques, and procedures used by cyber criminals, allowing them to better defend against these threats.
Solution for Threat Intelligence
One solution for implementing threat intelligence in cyber security is to invest in threat intelligence platforms that can automate the collection, analysis, and dissemination of threat information. These platforms can help organizations stay ahead of emerging threats and respond quickly to any potential security incidents. Additionally, organizations can also partner with threat intelligence providers to gain access to real-time threat data and analysis.
Information about Threat Intelligence
Threat intelligence can include a wide range of information, including indicators of compromise (IOCs), malware signatures, IP addresses, and domain names associated with known threats. Threat intelligence can also include information on threat actors, such as their motivations, tactics, and targets. This information can help organizations understand the risks they face and take appropriate measures to mitigate those risks.
Benefits of Threat Intelligence
There are many benefits to implementing threat intelligence in cyber security. Some of the key benefits include:
Reduced risk of a data breach
Improved incident response times
Enhanced visibility into emerging threats
Better understanding of threat actors and their tactics
Increased confidence in security posture
Challenges of Threat Intelligence
While threat intelligence can provide valuable insights into potential security threats, there are also challenges associated with implementing and maintaining a threat intelligence program. Some of these challenges include:
Overwhelming volume of threat data
Difficulty in identifying relevant threats
Lack of skilled personnel to analyze and act on threat intelligence
Cost of implementing and maintaining threat intelligence tools and services
Integration with existing security systems and processes
Conclusion
Threat intelligence plays a crucial role in protecting organizations from the ever-evolving landscape of cyber threats. By staying informed about potential risks and vulnerabilities, organizations can take proactive steps to defend against cyber attacks and minimize their risk of a breach. Implementing a robust threat intelligence program can help organizations stay one step ahead of cyber criminals and safeguard their digital assets.
FAQs
1. What are the key components of threat intelligence?
The key components of threat intelligence include indicators of compromise, malware signatures, threat actor information, and analysis of emerging threats.
2. How can organizations leverage threat intelligence to improve their security posture?
Organizations can leverage threat intelligence by using it to inform their security measures, enhance their incident response capabilities, and stay ahead of emerging threats.
3. What are some common sources of threat intelligence?
Common sources of threat intelligence include security vendors, government agencies, industry groups, and threat intelligence platforms.
4. How can organizations overcome the challenges of implementing threat intelligence?
Organizations can overcome the challenges of implementing threat intelligence by investing in the right tools and services, training their personnel, and integrating threat intelligence into their existing security processes.
5. What are the potential risks of not having a threat intelligence program in place?
The potential risks of not having a threat intelligence program in place include increased vulnerability to cyber attacks, slower incident response times, and higher risk of a data breach.
threat intelligence in cyber security